Complying With UAE NESA
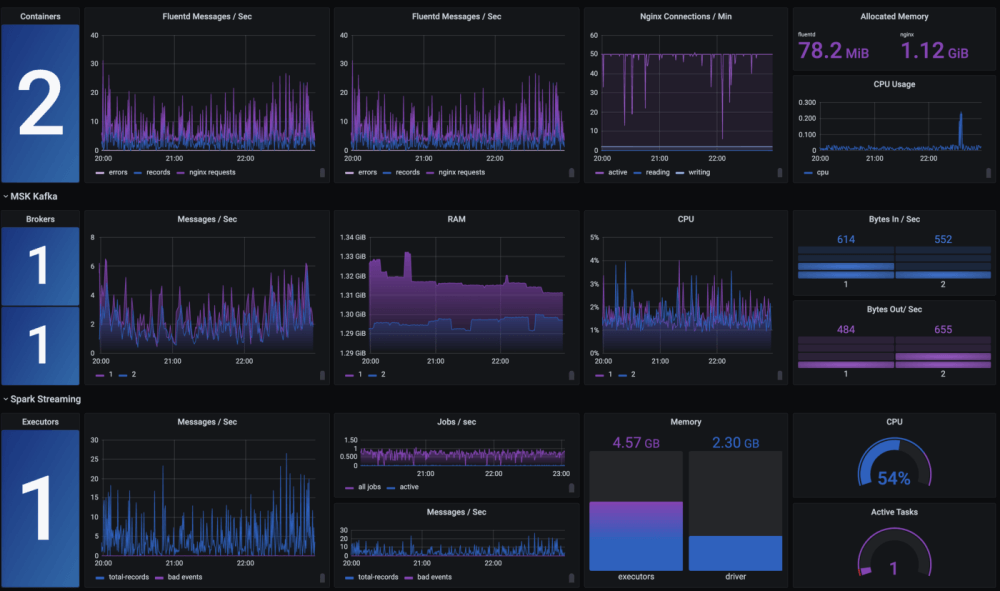
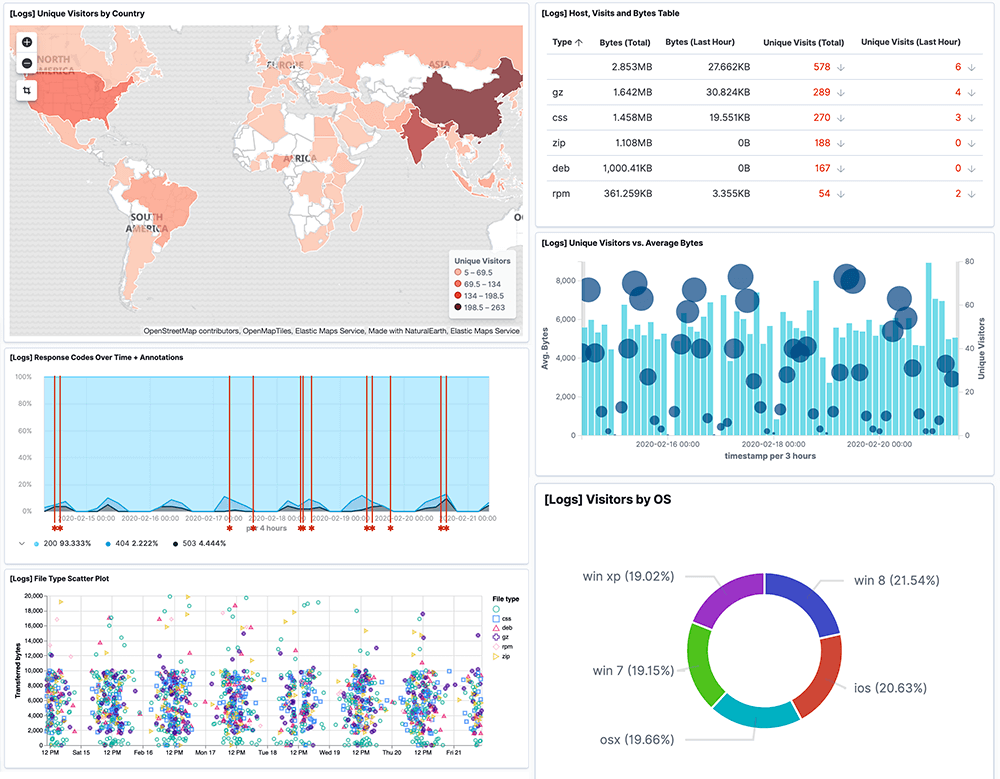
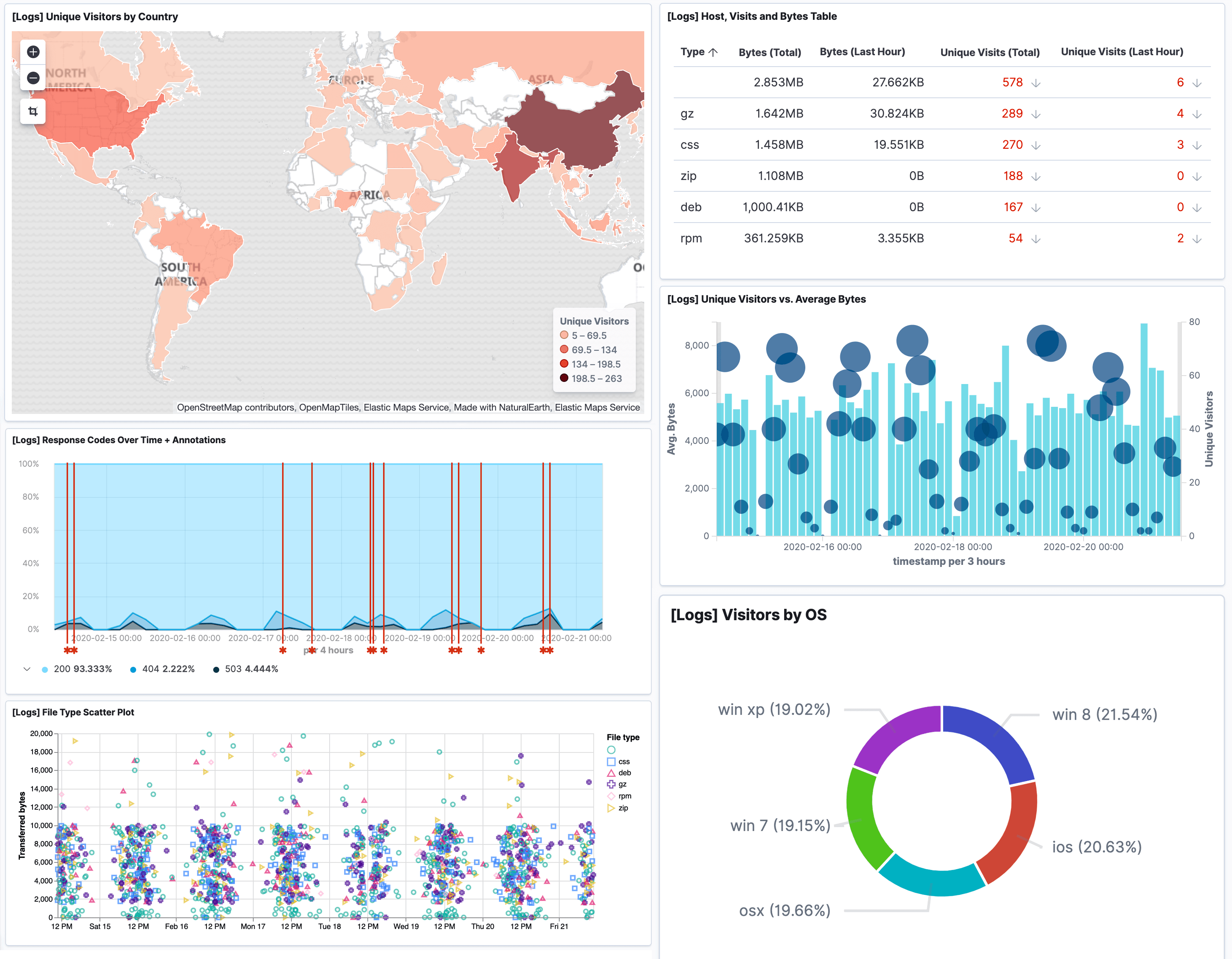
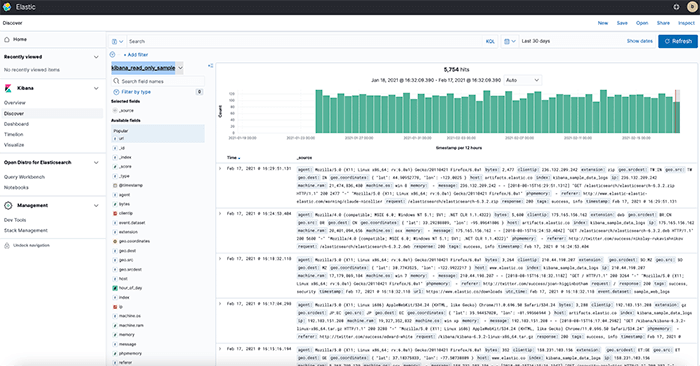
A national authority for cybersecurity in the United Arab Emirates (UAE), the National Electronic Security Authority (NESA), is making strides to protect critical sectors from cyberattacks. A mandatory set of standards has been developed by NESA for government organizations, semi-government groups, and business entities that are identified as critical infrastructure to follow.
However, not all of these organizations are capable of implementing the guidelines on their own. It is, fortunately, possible to solve many issues around meeting compliance by using Logit.io.
Interested in learning more about how Logit.io can help you meet the UAE NESA auditing criteria? Sign up for a free 14-day trial or book a call with one of our compliance specialists to find out how we can help you.