Why You Should Comply With GLBA
As part of the Gramm-Leach-Bliley Act (GLBA), also known as the Financial Modernization Act of 1999, the US government enacted legislation to ensure the protection of customer information. It is mandatory for financial institutions to conduct security risk assessments in order to comply with the GLBA requirements. Financial institutions also need to develop and implement security solutions that effectively detect, prevent, and allow them to respond to incidents in a timely manner. In addition, they are also required to conduct audits and monitoring of the security environment in which they operate.
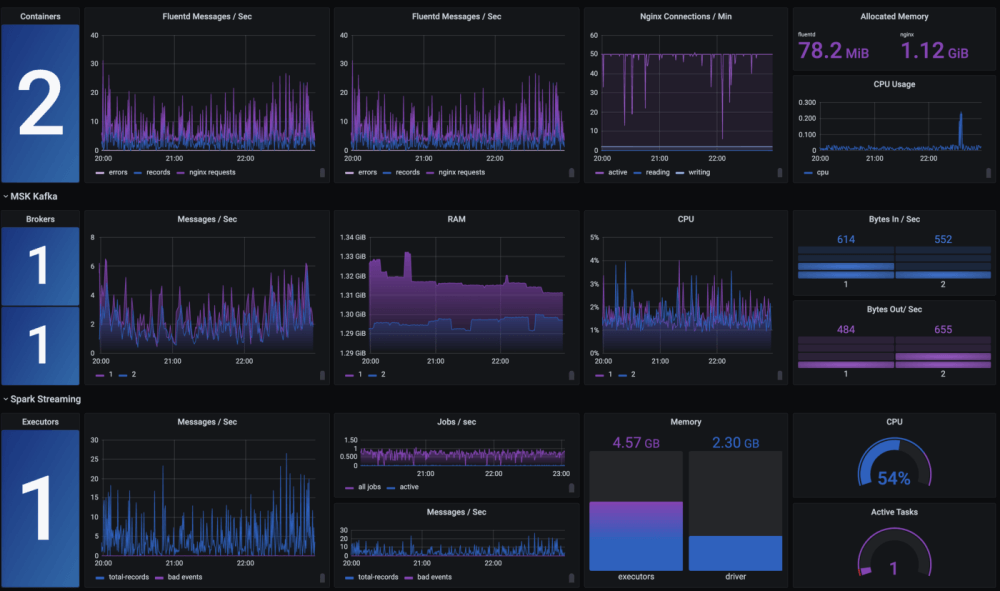
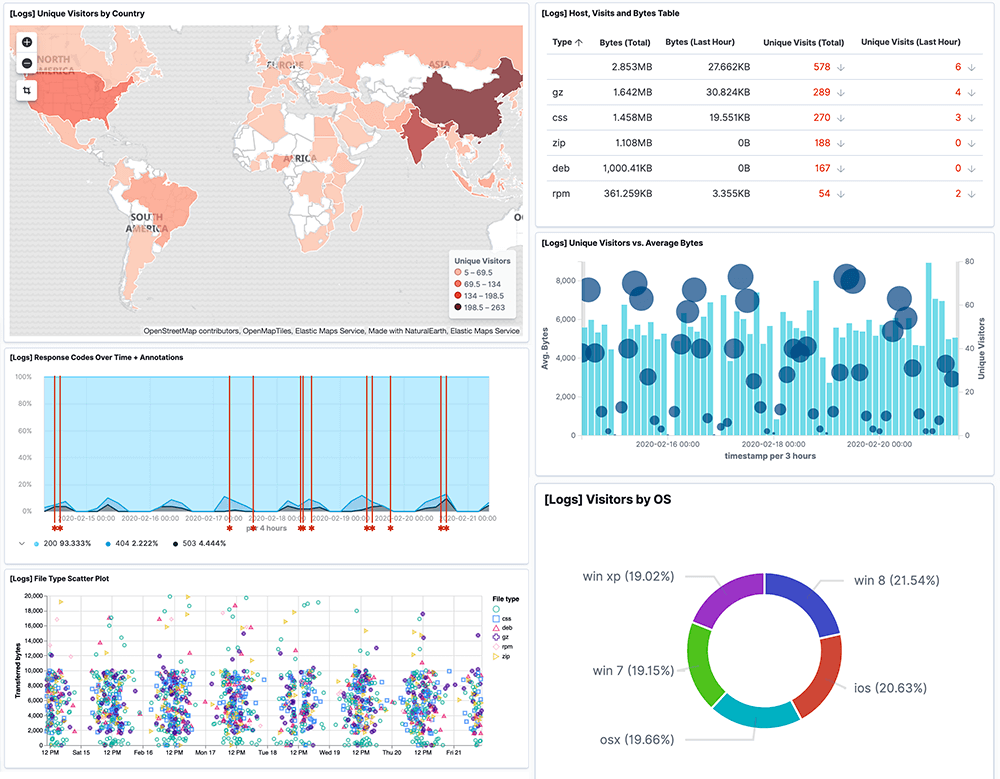
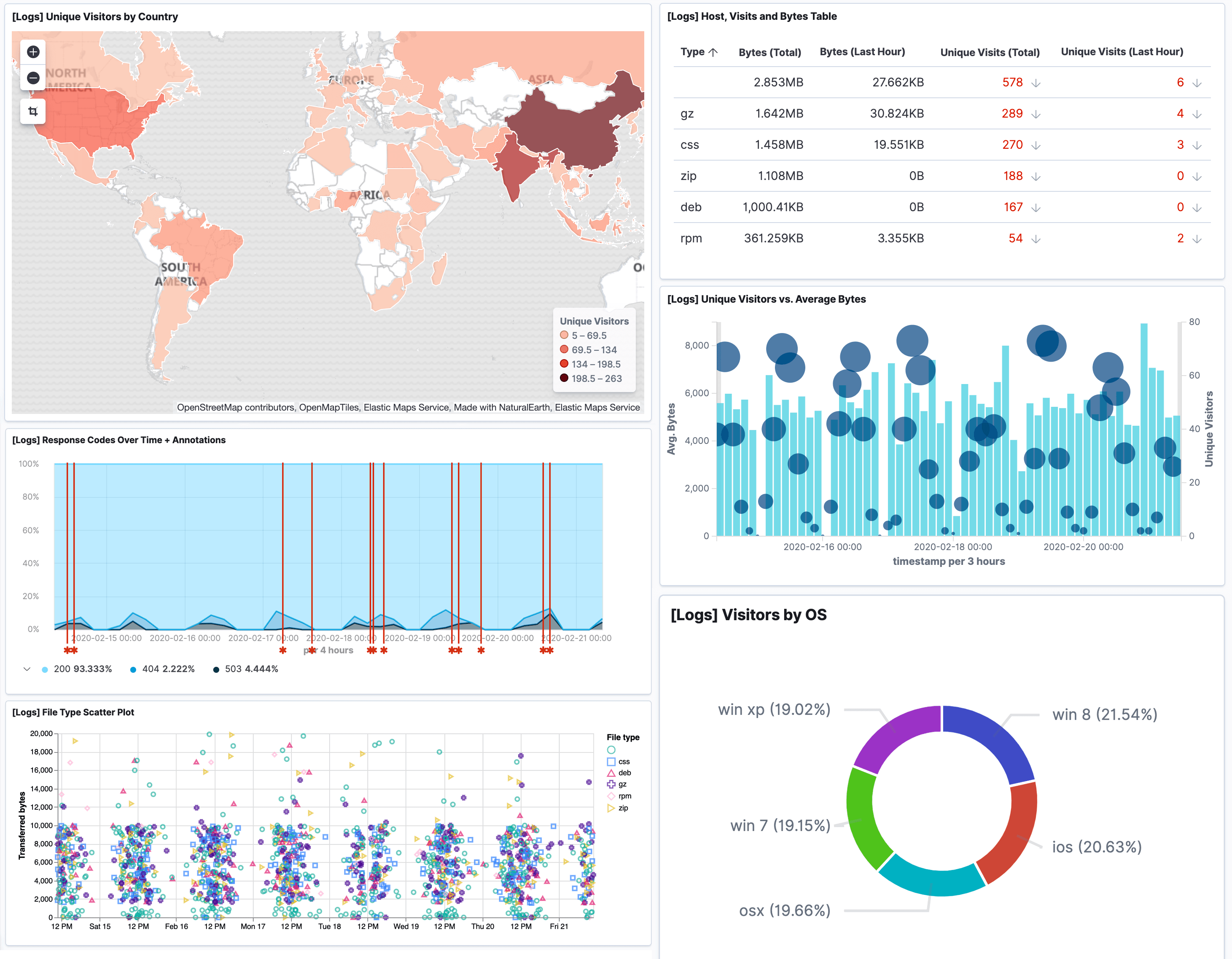
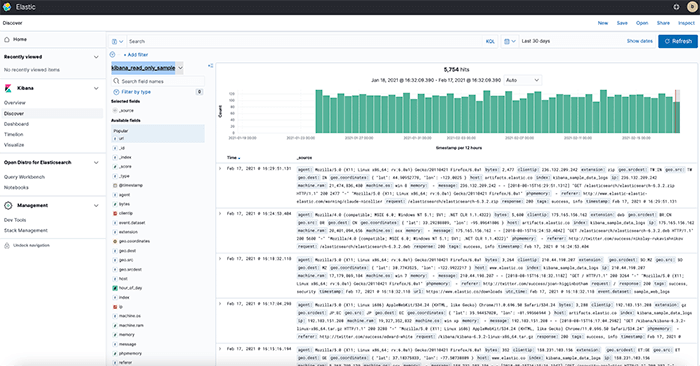
In order to meet many of the requirements of the GLBA, log data has to be collected, managed, and analyzed. By using Logit.io, many GLBA requirements can be directly met and the cost of complying with others can be dramatically reduced.
With Logit.io, you can monitor activity and conditions on your network in real-time by collecting log data from various hosts, applications, and network devices. Additionally, Logit.io provides you with real-time event monitoring, alerts, and reporting in order to help you stay compliant. Get a free 14-day trial of our compliance software today or schedule a call with our compliance specialists to find out more about how we can help you.